Projects
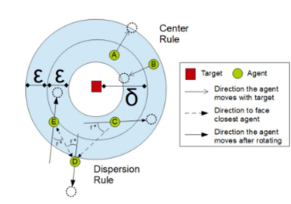
This project focuses on developing stable multi-agent coordination methods for target encirclement under uncertainty, emphasizing computational efficiency, resilience, and deployment on edge hardware to enable robust, real-time swarm autonomy.
We aim to test whether generative AI can insert malicious RTL into hardware designs and evade detection by verification. Our experiments will use a large RISC-V processor on an FPGA and smaller modular designs, all with existing formal verification in place.
We aim to implement an ultra light-weight peer-to-peer IoT network using the CHIRP communication algorithm.

Focused on detecting unique software behavior by monitoring hardware-level signals.
Researching AI based Trojan Attack on different parts of the FPGA development lifecycle. From HDL to Bitstream, how can AI developed trojan attackers affect FPGAs performance and efficiency while remaining unknown until attack.
We aim to implement a novel modification to a well known cryptosystem to build a framework and accelerator that enable secure computation by allowing operations on encrypted data. We aim to be more secure than traditional computation while faster than FHE.

We aim to explore how information theory concepts, such as entropy, can be applied to improve power estimation and guide power-driven optimization in hardware designs. The project will investigate both the accuracy of entropy-based estimation methods and their effectiveness in reducing power through optimization strategies.
Using techniques common in malware detection evasion create encrypted components that perform standard operations with a constantly changing key.
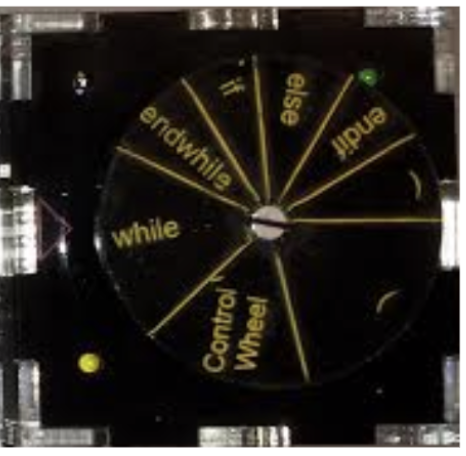
Create a block that based on orientation and manipulations performs one of several fundamental operations. When blocks are placed together they form more complex actions. Blocks should be ultra low-power and cost under five dollar per unit. End product should contain at least 25 blocks. See results from V1 completed by PDX Senior Capstone team circa 2015 and V2 completed by UCF 2024 team.
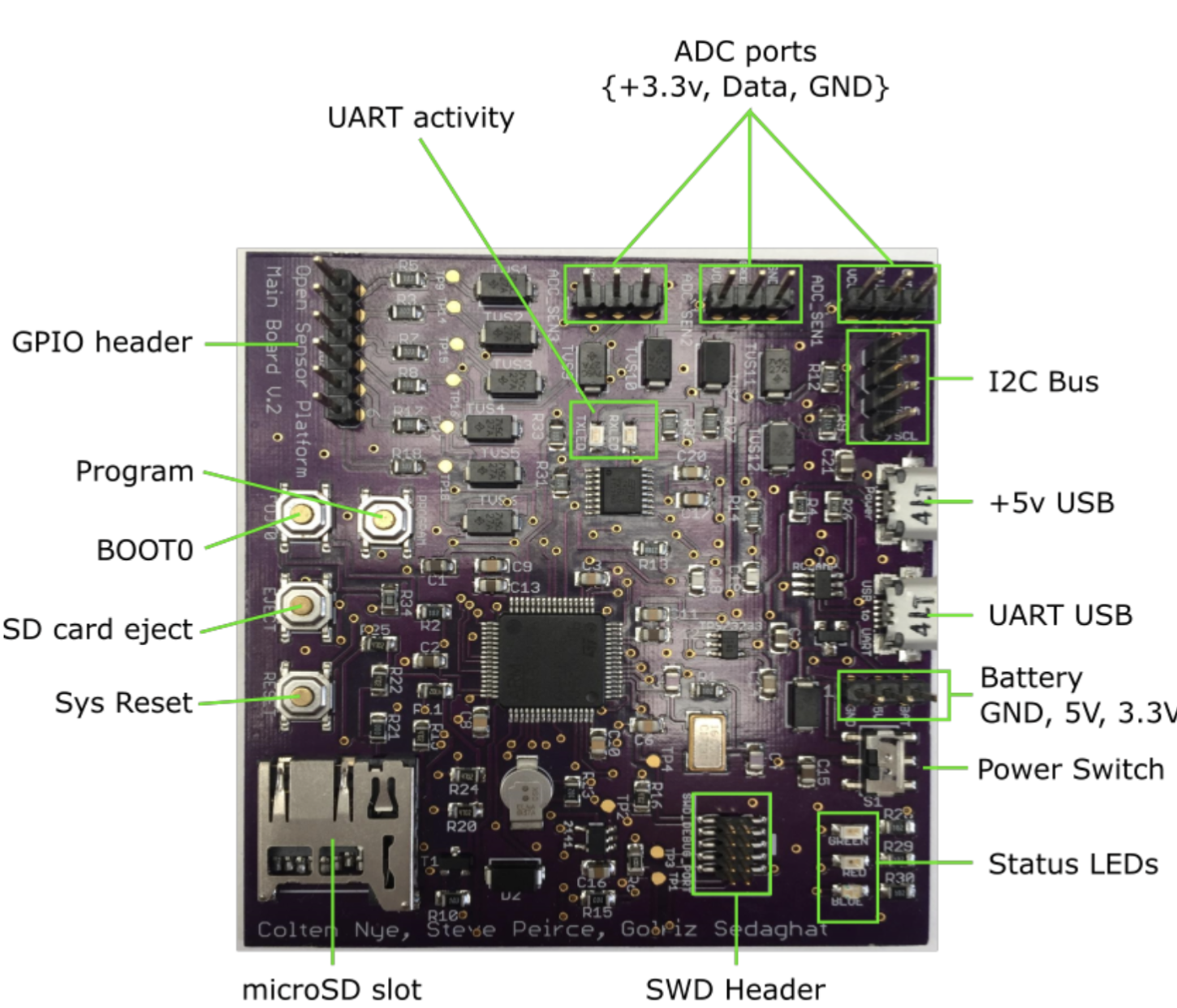
Create a data collection platform that allows for basic environmental data collection for at least three different properties (e.g., temperature, weight/pressure, brightness). Trading off sensor accuracy for simplicity is critical. Platform should allow end user to input the model that converts raw data measurements into known units. See results from V1 completed by PDX Senior Capstone team circa 2015 and V2 completed by UCF 2024 team.

Develop a 2^n x 2^n Grid of RGBW+ LEDs that is fed from the simulation output of a cycle/turn-based multi-agent simulator. Enable connectable components to increase the grid-size. Basic version should feature fixed 3D printed topology with each unit square being illuminated via an RGB+ led - stretch goal should feature pneumatically controlled tube structures and a flexible membrane.

Develop a micro-drone (<250g) with main-body continuously spinning at specific RPM; drone must still be fully controllable in XYZ. Preference toward hardware (PID) control system approach to spin correction. Spinning main body must be able to hold distance sensor.Telemetry and sensor data should be reported back to base controller.

Create a FPGA-based system that can generate and test memristors. The system should be able to generate a pattern, write it to a memristor, read the pattern back, and compare it to the original pattern.


This research project focuses on understanding the security implications of memristor devices. The goal is to identify potential vulnerabilities in memristor devices and develop countermeasures to mitigate these vulnerabilities.

This research project focuses on detecting hardware trojans using side channel analysis and machine learning. The goal is to develop a methodology to detect hardware trojans using side channel analysis and evaluate the effectiveness of the methodology on different hardware trojans.

The current focus of this research project is to build upon existing research on side-channel-resistant architectures using partially homomorphic encryption. Our goal is to test and analyze how these systems will work in hardware, rather than just in simulation